Bring Your Own Key (BYOK) in Microsoft 365: Take Control Where It Matters Most
Imagine this…
You’ve moved to Microsoft 365. Your emails, files, Teams chats, sensitive project documents — everything is in the cloud. It’s secure, encrypted, and backed by Microsoft’s massive infrastructure.
But here’s the big question 👇
Who actually controls the encryption keys?
The default answer? Microsoft.
But for organizations with strict compliance mandates, sensitive IP, or zero-trust philosophies, that’s just not good enough.
That’s where BYOK Bring Your Own Key steps in. And it’s a game changer.
🎯 What Is BYOK in Microsoft 365?
BYOK gives you — the customer — the power to create, own, and manage your encryption keys used to secure your Microsoft 365 data at rest.
In other words:
✅ You bring your key
✅ You store it securely in your Azure Key Vault
✅ Microsoft uses your key to encrypt your data
✅ And you remain in full control
You can rotate the key. Revoke it. Monitor access.
If you ever need to pull the plug — whether for compliance or crisis — you hold that power. Microsoft doesn’t.
💡 Why Organizations Choose BYOK
🔒 Data Sovereignty
You might be operating in a highly regulated industry — banking, healthcare, defense — or under strict data residency laws. BYOK ensures your keys never leave your control.
⚖️ Compliance-Driven Encryption
For many certifications (like ISO 27001, GDPR, or NIST standards), it’s not enough to encrypt — you need to demonstrate key ownership.
🚫 Kill Switch Control
If a breach occurs or you need to isolate data, revoking the key renders the content unreadable, instantly. It’s like flipping a switch — and only you have access to it.
👁 Transparency & Auditability
With Azure Key Vault logging and Microsoft Purview integration, you gain full visibility into who accessed what and when.
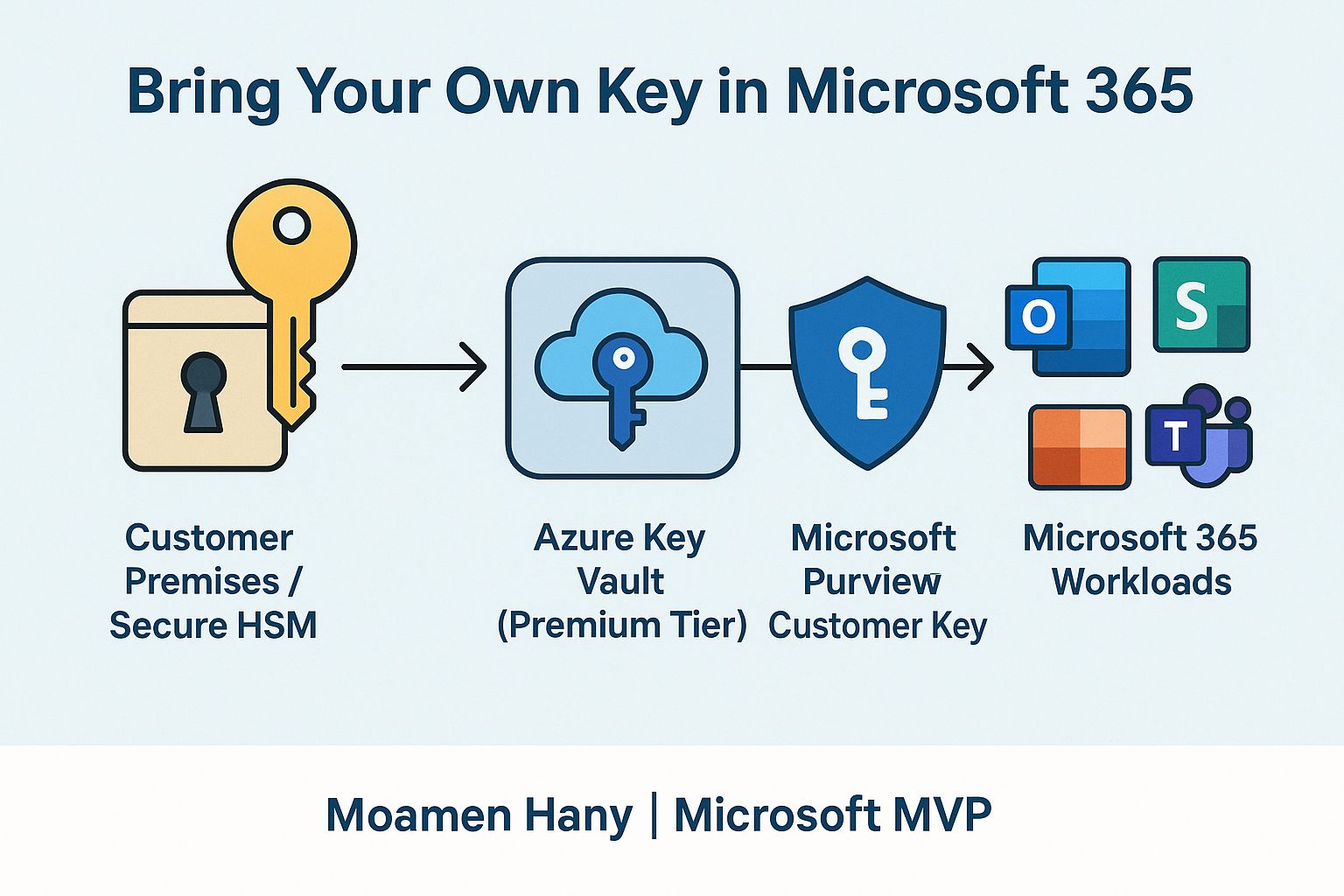
🧩 How It Actually Works
Let’s break down the flow simply:
- 🛠 You generate the encryption key
Typically using a Hardware Security Module (HSM) or secure key management process. - ☁️ You import it into Azure Key Vault (Premium)
A highly secure, cloud-based HSM environment fully managed by you. - 🔐 Microsoft 365 is configured to use your key
Via Microsoft Purview Customer Key integration, it links to your key in Azure Key Vault. - 📧 Your data is encrypted at rest in:
- Exchange Online
- SharePoint Online
- OneDrive for Business
- Microsoft Teams
- Planner, Viva, Loop, and more
- 📊 Monitoring & Control
You can revoke the key at any time, rotate it based on policy, and track all usage through logging.
🚀 Advanced Scenarios: What If You Need Even More Control?
👉 Double Key Encryption (DKE)
Think of this like two-factor encryption: one key stored in Microsoft’s cloud, and a second key stored on-prem or in your own key server.
Unless both keys are available, the data is unreadable even by Microsoft.
Ideal for:
- 🔐 National security workloads
- 🧬 Intellectual property
- 🚫 Full zero-trust, no-cloud-access models
🛠 Real-World Use Cases
💼 A law firm encrypts its client documents with its own key to meet strict privacy laws.
🏥 A healthcare provider uses BYOK to comply with HIPAA data-at-rest controls.
🏦 A bank ensures that even Microsoft can’t decrypt its financial records without explicit approval.
🏛 A government entity integrates BYOK with on-prem HSMs for national security classification.
💬 Final Thoughts: It’s Not Just Security, It’s Ownership
In today’s cloud-first world, moving fast is essential. But moving smart is critical.
BYOK isn’t just about encryption. It’s about empowering you to truly own your data — even when it lives in someone else’s datacenter.
And for many organizations, that’s no longer a luxury.
It’s the standard.
✍️ Want help building your BYOK strategy on Microsoft 365 and Azure? Or designing a compliant architecture tailored to your industry? Reach out — let’s make your cloud truly yours.
🔐💼 #Microsoft365 #Encryption #BYOK #AzureKeyVault #SecurityFirst #MoamenHany